What is the Likelihood That My Business Will Experience a Data Breach? [This and Other Cyber FAQs Answered]

If you could protect your business from a crime that would create hardship for your finances, reputation and operations, would you do it?
It’s a trick question.
Cyber crime is growing in severity and frequency, and yet, many businesses remain unprepared to respond to this kind of attack.
In our conversations with business leaders, we see that most companies are either on one side of the cybersecurity spectrum or the other: companies either are proactively and effectively addressing security, or they don’t have an accurate understanding of the topic and the danger associated with it.
There are many misconceptions about cybersecurity and what businesses should do to protect themselves. Unfortunately, these cyber myths often prevent businesses from taking the right actions at the right time.
Knowing the truth about your business’s risk in this area can make all the difference. That’s why we have outlined the most common questions that we hear from businesses about cybersecurity and provided the answers that can hopefully help you to think through how your company can begin to protect itself against cyber crime.
What should a business do to be effectively prepared for and protected against a cyber attack?
While each business is different and has unique needs, here are a few things that we recommend that all businesses pursue.
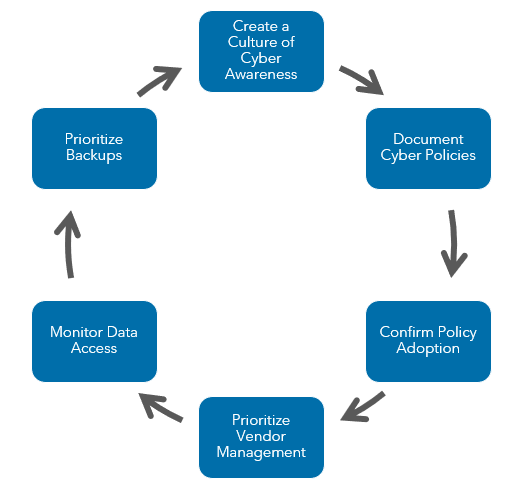
Create a culture of cybersecurity awareness
One of the strongest cybersecurity protection measures that you can take is to consistently train your employees and make them aware of cybersecurity risks.
Develop and document cybersecurity policies and procedures
If a breach does happen, you’ll have a strategy in writing so that your organization can respond in a timely and effective way. Having policies and procedures but not documenting them may not be enough to protect your organization.
Confirm policy adoption
Ensure that your cybersecurity policies align with the practices of your organization, especially when it comes to the implementation and strategy of your company’s IT structure.
Prioritize vendor management
Ensure that your company’s vendors who have access to your information are taking appropriate steps to protect your information and protect you from experiencing an attack that isn’t your organization’s fault.
Monitor data access
Make sure that physical access to data is monitored. This includes creating complex password parameters for your applications.
Another must-have security component is an industry-leading multifactor authentication (MFA) tool in place for remote access and overall network protection.
MFA simply adds an additional layer to the verification method to ensure that the proper people are able to gain access to your data and those with malicious intent are kept out.
Prioritize backups
Establish backups for your business’s data, and determine that they would be successful in backing up your information in the event of a breach.
How likely is it that my business will experience a cybersecurity breach?
The short answer is that all businesses have a likelihood of experiencing a breach.
A multitude of different factors turn companies into targets for a cyber attack, and there are some activities that may make your business more or less susceptible, but one thing is certain—each and every business that uses the internet has at least some risk for a cyber attack.
One of the most prominent myths in the realm of technology is that one industry is more susceptible than another industry. In reality, the more data that your business collects and stores, the more susceptible it is to attacks, regardless of your organization’s industry, size or location.
Is my business at less risk because it’s small?
The truth is that small businesses are just as attractive—if not more attractive—to hackers as large companies, and over half of attacks target small organizations.
Large companies often have their own internal technology team, whereas many hackers hope that small businesses may not have the knowledge or resources to effectively protect themselves in all areas.
If your company uses the internet to operate and conduct business, a cyber breach is a real possibility, and no organization is immune.
When should a business start to focus on cybersecurity?
Companies should always be looking at the topic of cybersecurity with a two-part approach: prevention and detection.
Both are needed to protect companies, and companies should constantly be considering each and seeking to understand their current situation in both areas.
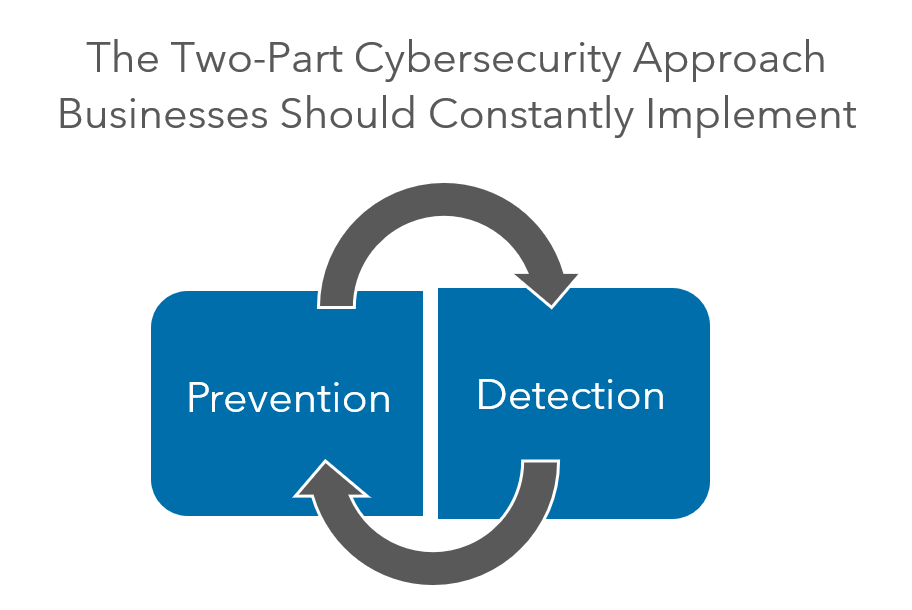
Unfortunately, for businesses that aren’t prioritizing understanding the issue of cybersecurity and protecting against it, it’s often too late when they realize they need to implement cybersecurity protection measures.
If your business truly is looking to protect itself from a security breach or cyber attack, there is no time like the present.
What is cybersecurity insurance, and does my company need it?
The purpose of cybersecurity insurance is to indemnify your company from a loss associated from a cyber attack or data breach, and it’s a helpful piece of any company’s effective cyber protection program.
What companies often don’t realize is that when a cybersecurity insurance claim is filed, an insurance company will check to ensure that your business has conducted due diligence to prevent the breach.
Cybersecurity insurance is only effective if it is paired with solid due diligence procedures.
Which employees should be charged with designing and facilitating my company’s cybersecurity practices?
All of them.
Often, our team sees executives who say that their technology and IT teams take care of all cybersecurity measures, yet many internal technology teams lack guidance or information from leaders. It takes fueling an ongoing dialogue between a company’s leadership and its IT department to effectively protect against risk.
In addition to those employees who are charged with designing and implementing cybersecurity policies and procedures, each employee at your organization should have a strong understanding of the risks your organization faces and what practices they can implement in their own roles to prevent a security breach.
Moving Forward with Cybersecurity for Your Business
Having an accurate understanding and thorough knowledge of your business’s risk positions you to create an effective strategy to protect yourself, but the work is never done.
Businesses should constantly be analyzing trends, reviewing risk and adapting policies and procedures to ensure that they are protected now and into the future. Maintaining a current knowledge of the world of cybersecurity, as well as your business’s operations and risks, is the foundation of a successful cyber protection strategy.
For answers to other questions or to gain insight about what an effective cybersecurity program might look like at your specific organization, request contact from a Warren Averett cybersecurity expert.
This article was originally published on September 18, 2019 and most recently updated on July 22, 2022.

