
Customer confidence is one of the most valuable business assets you have. Yet, customers increasingly require extra assurance that your company is doing its due diligence to develop and maintain excellent financial integrity and solid cybersecurity health. In today’s business climate where options are plentiful, customers have a distinct method to assist in determining the operational integrity, reliability and security of the service organizations with whom they work.
This comes in the form of a System and Organization Controls, or SOC report.
If your customers have not asked you for a SOC report yet, it’s likely only a matter of time. Especially for your customers that must adhere to certain laws and regulations or those that practice good vendor management, obtaining a SOC report from your service organization may be a necessity for them.
However, understanding the broad range of SOC reporting options and the type of report that you need is not always straightforward. That’s why we’ve created this essential SOC primer. In this guide, we will examine the differing types of reports in detail, how to obtain an examination, how to use SOC report results and reasons why a SOC report can benefit your company.

As defined by the American Institute of Certified Public Accountants (AICPA), SOC reports are a suite of reports that are produced as part of an audit or attestation examination of your company’s internal controls—the processes your company has put in place to ensure financial information is accurate or data is protected and handled appropriately.
In a SOC examination, independent certified public accountants (CPAs) examine and provide respected professional opinions on various aspects of how a company handles certain important matters, depending on the services provided by the company and other circumstances.
The data provided will shed light on safeguards that are in place to protect financial reporting and/or data security and, in some cases, reveal if the systems and controls are working effectively and consistently.
The SOC report is the outcome of that examination. The audit identifies, outlines and validates that your organization has (and uses) appropriate internal controls over your information systems.
Many companies opt to obtain a SOC report because it helps to build trust with customers. By having an independent CPA review and report on the organization’s systems and controls, customers can verify that your company is maintaining high standards for business integrity. This goes a long way to retain the customers you have while also helping you to acquire new ones—a win for everyone involved.
However, the benefits don’t end with customer confidence. SOC reports also provide substantial insight that can help your business improve security and potentially avoid costly errors.
Even if your organization already has strong controls in place, a SOC report can help you better understand where you may need additional processes and controls to protect your organization and your clients’ financial and confidential information. When used correctly, SOC reports also outline important steps that will help your company bolster security now and in the future.
Not only is a SOC report crucial to setting your organization up for success, but it can also be transformed into a blueprint for organizational process improvement. Additionally, it becomes an important differentiator in the marketplace when your competitors have not yet taken the step. Potential customers will take into consideration that your business puts additional safeguards in place and understands the risks inherent with handling customer data.
The primary aim of a SOC exam and report is to gain clarity and knowledge for your company, your customers and your vendors, which means that its primary use lies in how your company applies what you’ve learned from its findings.
SOC reports help companies identify processes and procedures that need to be reworked or refined and recognize those items that are being done well. This, in turn, leads to the chance to grow and improve, as well as to communicate the value of your controls to your current and prospective customers. Understanding and applying the information gained from a SOC report is discussed in detail in Chapter 6.
In sum, a SOC report is an asset to the business, showing customers you value their information and take their trust seriously.
Choosing the right SOC report, and the right SOC report type, can lead to more clients, better security and increased trust in your organization. But with so many reports to choose from, you might be wondering which one your organization should pursue. Let’s take a quick look at the options available and then delve deeper in subsequent chapters.

A SOC 1® report, previously referred to as a SAS70 or an SSAE 16, is focused on controls at service organizations that can have an impact on a user entity’s financial reporting. It’s intended to report on activities that pertain to the organization’s financial processes and offer information about the effect the service organization’s controls have on the user entity’s financial reporting.

Organizations needing a SOC 1 report find them useful in evaluating their internal controls and determining if they are effectively managing or mitigating risks to their business objectives. They are also utilized when user entity auditors plan and perform financial statement audits.
There are two types of SOC 1 reports: Type 1 and 2.
SOC 2® reports are designed for a broader range of users than SOC 1 reports. Because they revolve around an organization’s security, among other elements, there is a wider range of service organizations and user entities that a SOC 2 report applies to.
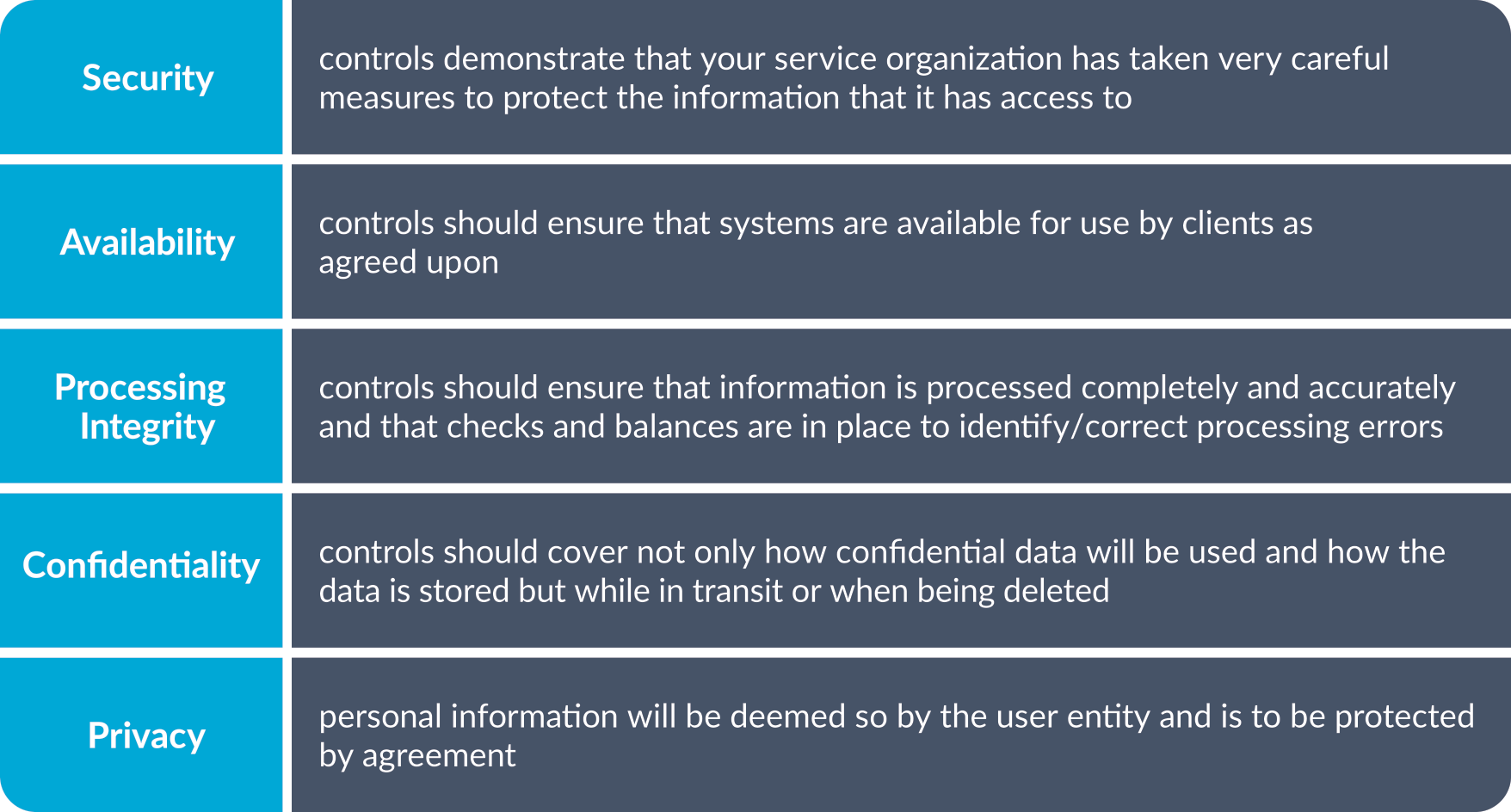
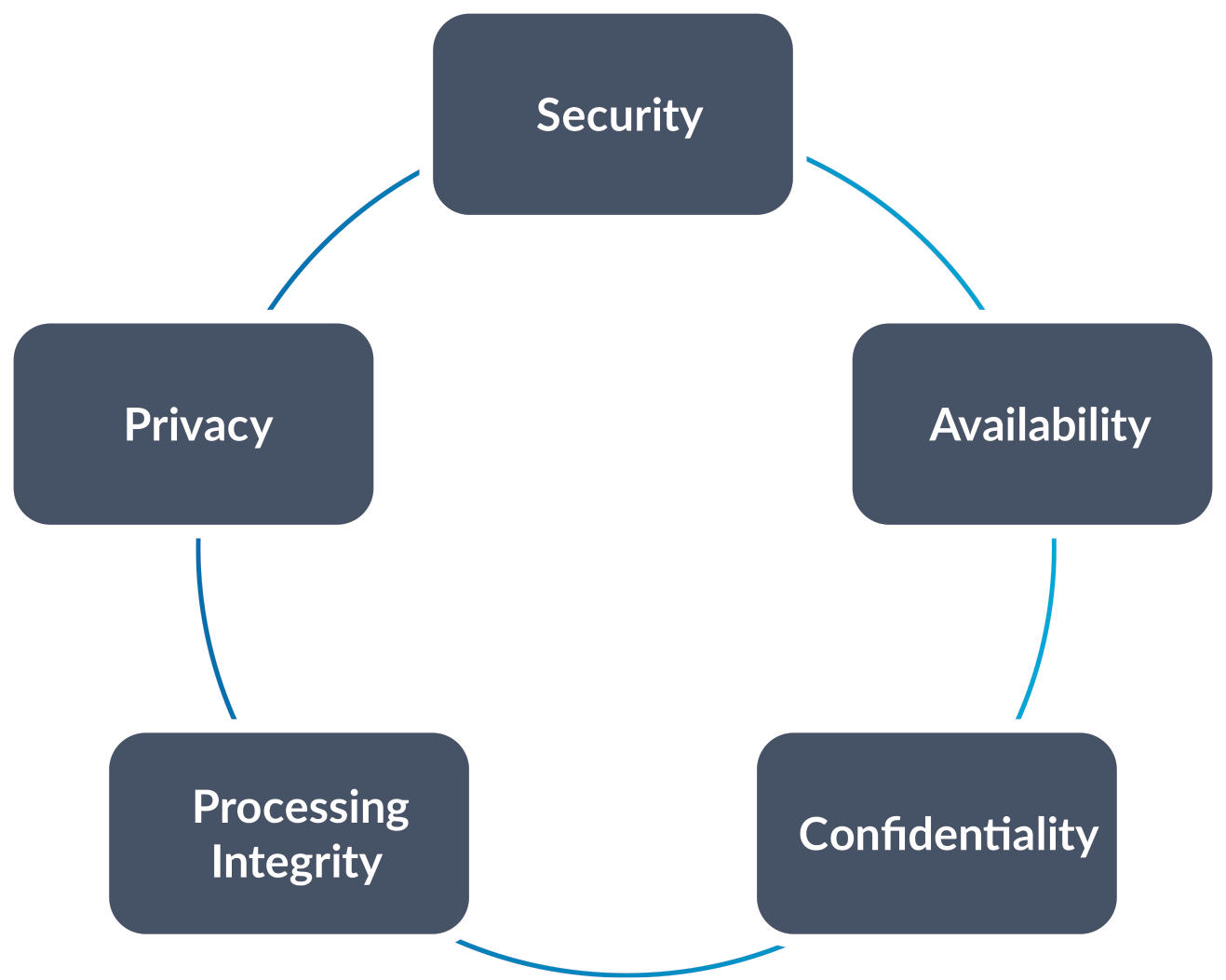
With SOC 2, the focus is non-financial controls. The report is intended to help users understand the internal controls of a service organization across these five trust services categories:
While the SOC 2 report can be helpful for internal improvement and evaluation of the non-financial controls that it’s focused on, the need is usually driven by customers.
There are two types of SOC 2 reports: Type 1 and 2.
SOC 3®: While the requirements for performing a SOC 3 examination are similar to the SOC 2, the report is shorter and more high level than the SOC 2 report. According to the AICPA,
“These reports are designed to meet the needs of users who need assurance about the controls at a service organization relevant to security, availability, processing integrity confidentiality, or privacy, but do not have the need for or the knowledge necessary to make effective use of a SOC 2 report. Because they are general use reports, SOC 3 reports can be freely distributed.”
SOC for Cybersecurity reports consider an organization’s cybersecurity risk management program and entity-wide controls.
SOC for Supply Chain reports address the AICPA Trust Services Criteria relevant to the same trust services categories used in a SOC 2 report. Specifically designed for manufacturers, producers and distributors, these reports assist supply chains in effectively communicating controls in place over production and distribution risks in their systems.
Determining which report you need will depend on what services your organization provides to your customers, how you plan to use the information gained from the findings and to what extent your internal controls will be examined.
Of the five reports, SOC 1 and SOC 2 are by far the most common for companies to need or for your customers to request. We address both in depth in the following chapters.

As previously mentioned, the SOC 1 report addresses the internal controls of a service organization and the effect those controls may have on a user entity’s financial statements. If the services your organization provides to your customers could have an impact on their financial statements, you’ll likely be asked to provide a SOC 1 report.
The uses of SOC 1 reports are varied; they incorporate insightful information that can be used to give assurance over an organization’s controls that impact their customer’s financial reporting.
A service organization can utilize a SOC 1 report to help them understand the impact and effectiveness of the internal controls they have in place to address risks to the organization. Should a SOC 1 report find issues with the existing controls, an organization can use that information to target areas of improvement.
Through a SOC 1 report, organizations can also gain information about the existence and effectiveness of their internal controls to positively impact a user entity’s financial statements. And user auditors can wield these reports when planning and performing audits on a user entity’s financial statements.
The SOC 1 report is important for proving to user entities that the service organization is taking commercially reasonable precautions and that they are considering and addressing any risks related to services they provide.
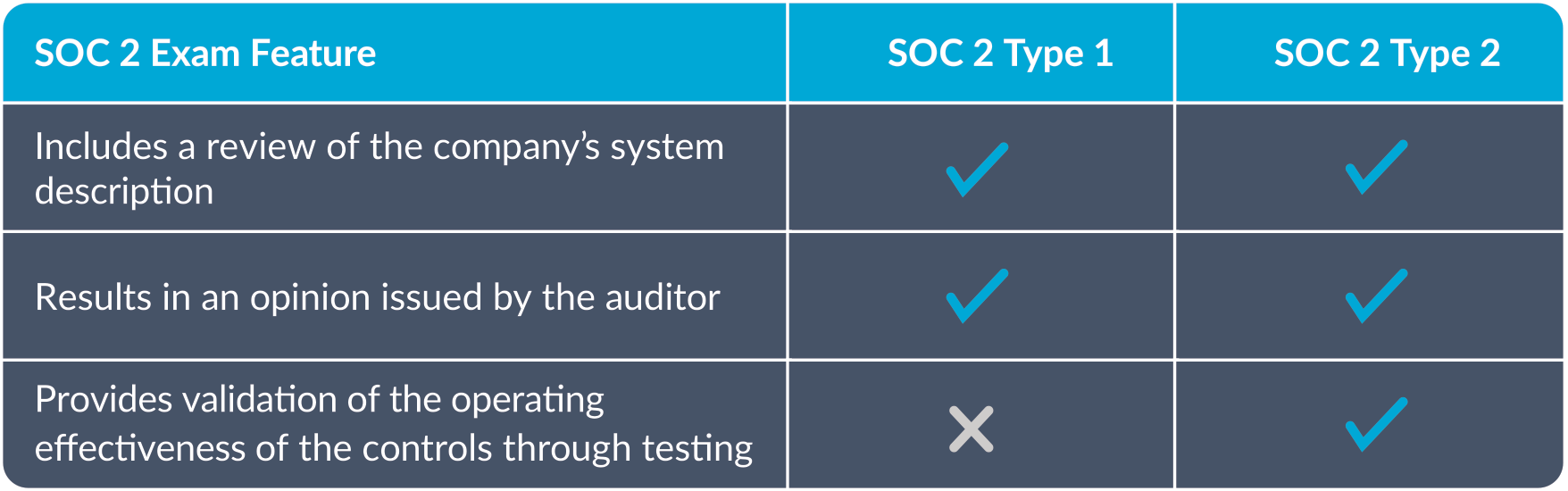
The process for a SOC 1 Type 1 report is rather straightforward. An auditor reviews the organization’s system description to ensure that it is fairly presented and evaluates whether controls are suitably designed as of a specified date. Testing is minimal, typically an example of one for each control.
With a Type 1 report for SOC 1, it is up to an organization’s management to identify which internal controls exist within the organization regarding financial reporting. Then, those controls are reviewed by a qualified CPA and evaluated for the suitability of the design and fair presentation of the system description (controls narrative) as of a specified date regarding the services provided.
A SOC 1 Type 2 report builds on the information in the SOC 1 Type 1 report but goes a step further by evaluating the controls over time. This type of report includes the actual detailed testing of those controls to determine they are operating effectively for a period of time (usually six to twelve months).
As such, a SOC 1 Type 2 report extends the Type 1 report by including detailed testing of your controls throughout a period of time. Testing is performed on the controls surrounding your organization’s processes and procedures specifically related to the services that your organization provides.
A SOC 1 Type 2 report has no specific criteria for testing, unlike SOC 2 reports. However, the service organization must define what control objectives are relevant to the services they provide and identify the controls they have implemented to meet each control objective.
To begin the process for a SOC 1 Type 2, your organization defines your system and provides your independent, third-party CPA auditor with descriptions of your controls—much like you’d begin a Type 1 report. The SOC auditor will then evaluate and test those controls.
Taking the time to obtain a SOC 1 Type 2 report sends a clear signal to both your customers and competitors about your commitment to transparency and accuracy. It demonstrates that you will commit to an ongoing process. Also, having a Type 2 report offers an organization a competitive advantage over its competitors that have only completed the Type 1 or don’t have a SOC 1 report at all.
The SOC 1 Type 2 report can be an important vendor management consideration for your customers as well. If your customers are not already doing their due diligence to ensure that the service organizations or vendors they work with are doing everything they can to protect customers, they will be soon.
In summary, a Type 2 report differs in scope and testing. Type 2 extends past the defined system description and design of controls to include testing of those controls. The emphasis goes beyond the existence of the controls to their operating effectiveness over the long haul.

The SOC 2 report is more involved and has a different focus. SOC 2 reports are most common for businesses that handle, process or manage data. This includes but is not limited to Software as a Service (SaaS) providers, data centers, cloud service providers and managed IT providers.
The SOC 2 report focuses on a service organization’s security controls. It is also an attestation report in which an organization’s management identifies certain internal controls that have been designed and implemented, and those controls are audited by a qualified CPA firm.
What differentiates a SOC 2 report is the depth and breadth of information provided that can be helpful in handling data security appropriately. Because a SOC 2 report considers security and internal IT controls relating to key trust services criteria, organizations can use the reports as a check to validate that they are doing all they can to secure data and handle it appropriately. The trust services criteria outlines five categories that can be included in the reports: security, availability, processing integrity, confidentiality and privacy.
What’s most important to remember is that the security category (also known as the “Common Criteria”) is foundational. It incorporates organization-wide components of internal control as defined in the COSO framework and also IT security/cybersecurity related criteria. Other categories may be added as applicable to the services you provide and are integral to the service commitments made to your customers.
Because service organizations that complete SOC 2 reports handle information for their user entities in a variety of ways, you’ll want to assess this carefully when determining which of the five key trust services categories to focus on for your report. Selection of the categories should be derived from the service organization’s service commitments and system requirements outlined to user entities. These are typically defined in agreements, contracts, or even on the service organization’s website. Management of the service organization then identifies the controls they have in place to meet the defined criteria for the selected categories.
A SOC 2 Type 1 report differs from the SOC 1 Type 1 report in focus but is similar in scope. Again, the Type 1 report is an attestation examination of a service organization’s suitability of design of its internal controls relevant to the trust services criteria as of a specified date. The system description for SOC 2 reports also must comply with certain standards as separately outlined by the AICPA in the DC Section 200 Description Criteria.
A SOC 2 Type 2 report can help uncover opportunities for improvement in your processes and procedures. With this report, you’ll extend the scope of the Type 1 report (description of a company’s systems and controls) to include the actual detailed testing of those controls over a period of time.
The focus in a SOC 2 Type 2 report is on the following functions:
Instead of being an examination limited to a specific date, the Type 2 report looks at the internal controls and includes the testing of those controls over a certain interval—usually six to twelve months.
A SOC 2 Type 2 report provides strong assurance about your organization’s commitment to security and protecting customer data. Customers may be able to outsource services, but they cannot outsource their responsibility for the data that has been entrusted to them. Your SOC 2 Type 2 report will ensure customers that your organization takes the security of their valuable data and information as seriously as they do.

When considering the process for getting a SOC report, it’s important to first consider the timeframe of these examinations.
Each report type takes an investment of time, of course, with Type 2 reports requiring a longer and more regular commitment since they test your controls over a period of time. Proactive organizations realize that waiting until asked for a SOC 1 or SOC 2 report may result in lost business. It can take weeks or months to have a report produced, and in the meantime, a client or a prospective client will likely seek services elsewhere, so it’s best to start early.
During this timeframe, three phases of the process occur that will culminate in the delivery of your SOC report.
The first step to preparing for a SOC exam is inquiry. Before beginning a SOC examination, start by evaluating your organization’s existing policies, procedures and internal controls. Are they adequate? Are they well designed? Will they prevent errors in reporting or reduce risk?
If your answers are not satisfactory or you are simply unsure, you’ll want to consider a readiness assessment. This assessment will help you in evaluating your existing controls to determine where controls can be strengthened or where they may be missing altogether. This process has one clear advantage: It provides the chance for your organization to create or edit your controls and shore up any gap areas before a full SOC exam is conducted.
Since time to obtain a report is often of the essence, you’ll want to have your readiness assessment long before a customer requests a SOC report from you.
Examination procedures and requirements will vary depending on the SOC report and type your company has requested. In general, this phase will consist of you providing information to fulfill your auditor’s requests to be able to complete the exam and form an opinion for the auditor’s report.
This can be a substantial amount of work for your company’s management, IT group or others responsible for gathering documentation, so providing a clear timeline and task list can help to mitigate issues.
Once your organization has completed a SOC examination, the auditor will issue a SOC report. Once your organization has completed a SOC examination, the auditor will issue a SOC report. The SOC report itself is what you’ll provide to your customers to prove that you have completed a SOC examination.
A SOC report is a package that includes:
We discuss how to use and understand the results of your SOC report in the following chapter.

It’s important to understand that SOC reports don’t come with compliance or certification, but rather an auditor’s opinion. Your customers will look for the auditor’s opinion to see how your organization’s controls faired in the exam, as opposed to an indication of SOC compliance or certification.
The auditor’s opinion represents the part of most significance to your customer. It will include information about:
Bear in mind that while no opinion indicates SOC compliance or SOC certification, there are several types of opinions that the auditor can give. The outcome of a SOC exam and results of the tests performed by the auditor is either that the auditor agrees with the specified controls and system description and provides an “unmodified opinion,” or they may provide a “qualified” or even “adverse” opinion when significant issues are found.
Let’s examine the three kinds:
No matter what kind of auditor opinion your organization receives, the outcome represents an opportunity. While an unmodified opinion in a SOC report is the preferred outcome, a qualified opinion is not a failure, but a chance to focus on the specific areas that should be improved to increase security and reliability. It can also provide insight into an organization’s adherence to its controls around regulatory requirements and corporate governance.
Upon receiving your SOC report, you’ll learn about the resources you need to identify blind spots, fix problems before they happen and determine which processes are effective. Because a qualified or adverse opinion, where an issue was found, documents the potential risk, it serves as a guide for implementation of new policies and controls—perhaps even a blueprint for training staff.
Here are a few examples of ways your organization may be able to fully leverage what you’ve learned from your SOC report:
All this information adds up to valuable insight that can be used to tighten up your security while simultaneously boosting customer confidence and potentially winning more business.

Trust is your company’s biggest asset. Why take chances with it? By finding a qualified and reputable SOC auditor, you can begin the path to greater transparency and detailed reporting surrounding financial practices and data security. Obtaining a SOC report demonstrates to your customers—current and potential—that you take risk management and data security seriously.
Knowing where to begin with SOC reporting can be daunting. There’s the matter of which report to choose as well as which criteria to focus on should you choose a SOC 2 report. This is one reason why working with experienced accountants who understand the complexities of the process is of utmost importance.
Warren Averett can be an indispensable partner in the SOC audit process. We’ve developed a thorough and comprehensive approach to a SOC Readiness Assessment that can give you peace of mind before you complete a SOC exam. Contact us today for more information on how a SOC report can improve your financial reporting, data security and your standing with customers.
