SOC Trust Services Criteria: A Crash Course

As companies outsource more tasks or entire functional areas to service organizations, trust becomes a critical factor. This is especially true if the service organization has access to or will be handling and processing sensitive information.
That’s where the System and Organization Controls (SOC) 2® report comes in; it’s intended to provide clients and potential clients of a service provider with a third-party assessment of internal controls regarding areas such as data security and availability through the Trust Services Criteria.
What are the SOC Trust Services Criteria?
The Assurance Services Executive Committee (ASEC) of the AICPA, in 2017 established a set of criteria to be used in SOC 2 reporting – the TSP 100 2017 Trust Services Criteria. These Trust Services Criteria provide a framework for evaluating the controls of a service organization in several key areas and are updated as needed. The framework was aligned with the Committee of Sponsoring Organizations of the Treadway Commission’s 2013 Internal Control – Integrated Framework (COSO framework).
The five categories defined as part of the Trust Services Criteria by the ASEC are:
- Security, also known as the Common Criteria
- Availability
- Processing Integrity
- Confidentiality
- Privacy
A service organization chooses those Trust Services Categories that relate to the services they provide.
SOC 2 reports must minimally include the Security Category, with others added as appropriate or required by a service organization’s user entities. The SOC Trust Services Criteria are well defined, so service organizations know what’s required of them and so user entities can effectively evaluate the SOC 2 report findings.
Not all SOC Trust Services Categories are appropriate for all service providers. A deeper look into each can point to which ones are right for your organization.
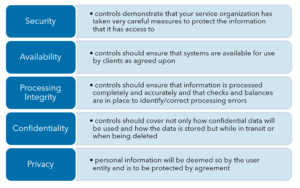
Security
According to the AICPA documentation, the Security Category is “Information and systems are protected against unauthorized access, unauthorized disclosure of information and damage to systems that could compromise the availability, integrity, confidentiality and privacy of information or systems and affect the entity’s ability to meet its objectives.”
The SOC 2 examination reviews the controls relative to security that demonstrate that your service organization has taken very careful measures to protect the information that it has access to.
This includes logical and physical access to key systems, code and infrastructure. There should also be controls in place regarding firewalls, passwords, user roles and network devices and their configurations, to name a few. Also addressed are the five internal control components of the COSO framework: control environment, risk assessment, control activities, information and communication and monitoring.
Availability
Turning back to the AICPA definition, Availability verifies that “Information and systems are available for operation and use to meet the entity’s objectives.”
Put more plainly, these controls should ensure that systems are available for use by clients as agreed upon. Availability controls would cover things like disaster recovery and business continuity plans.
While not applicable to every service organization, this may be a key Trust Services Category for cloud hosting, SaaS companies or API providers.
Processing Integrity
The Processing Integrity Category is defined as “System processing is complete, valid, accurate, timely and authorized to meet the entity’s objectives.”
Processing Integrity is a less commonly used criteria than the other categories. Service organizations may have access to and even store sensitive information, but those that process are a rarer breed.
This is an important category for service providers that process payments, for instance. It could also apply to a loyalty program provider or similar service. The controls related to Processing Integrity should ensure that information is processed completely and accurately and that checks and balances are in place to identify processing errors and correct them.
Privacy
Privacy controls protect and provide that “Personal information is collected, used, retained, disclosed and disposed of to meet the entity’s objectives.”
Personal information is the key for the Privacy trust services category. If your service organization handles personal information, be it the information of your customers, your employees or something else, the internal controls for protecting that information would be included here.
These controls should cover not only how the data will be used and how the data is stored but while in transit or when being deleted.
Confidentiality
Controls for the Confidentiality category should ensure that “Information designated as confidential is protected to meet the entity’s objectives.”
Confidentiality is different than privacy in that privacy is focused on personal information, whereas confidential information will be deemed so by the user entity and is to be protected by agreement.
Which SOC Trust Services Categories Should Be Included in My Report?
For a service organization, the categories that should be included in your SOC 2 report are determined by you. At a minimum, it must include the Security Category (Common Criteria), but from there, your organization can add whichever of the additional four trust services categories that apply to your business. The categories selected should reflect the policies, procedures and controls implemented by your organization to mitigate risks that could compromise the achievement of your organization’s service commitments and system requirements.

A helpful consideration when determining which SOC Trust Services Categories should be included would be what is requested or expected from your customers. Consider your business, services and what your clients would want to know to choose your services to be reassured about your internal processes.
While the Security Category is foundational, you should remember that adding more categories may not necessarily be better simply because there are more categories in your SOC 2 report. Only add the categories, in addition to Security, that are applicable to your business and your service commitments and system requirements. Additional categories are unlikely to help you if there is no business reason for you to have controls in that category.
Learn more about the SOC Trust Services Criteria
SOC 2 reporting can be a significant benefit to your business, helping you to establish trust and credibility with your customers and potential customers, offering you a competitive advantage and providing you with clear direction to improve your internal controls.
Warren Averett is here to help you realize all of those benefits.

