What Helps Protect from Spear Phishing? [5 Things Your Company Can Do Now]

Spear phishing has rapidly become one of the most successful hacking methods of our time.
In 2020, 75% of organizations around the world reported at least one successful phishing attack, and a majority of these attacks were attributed to spear phishing. If we stay on this course, every organization is likely to fall victim to a spear phishing attack unless protective actions are taken.
But when it comes to such a targeted and sophisticated cyber crime, how can you know what helps protect from spear phishing?
Here, we’ve outlined the basics of what spear phishing is, how it works and five specific actions that your company can take now to protect against it.
Download the eBook, How to Spot and Thwart Phishing Scams: A Guide for Businesses.
What is Spear Phishing?
Before we jump into what helps protect from spear phishing, it’s important to understand what typical phishing is, how spear phishing is different and how hackers often devise these plans to exploit companies.
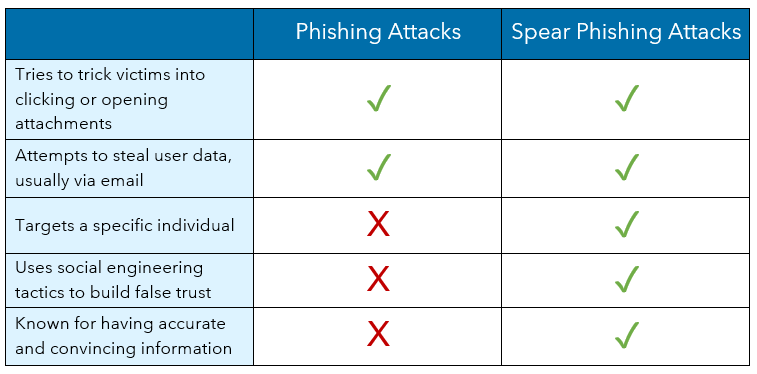
Typical Phishing Attacks
In phishing scams, a cyber criminal tries to steal user data by posing as a familiar or trusted entity in order to trick a victim into opening a message or clicking a link that then infects his or her system with malware.
These kinds of attacks are generic with no one intended target. However, as technology has advanced, so have phishing attacks, leading to a more targeted and damaging approach known as spear phishing.
Spear Phishing Attacks
Spear phishing is a type of phishing attack that is considered to be a more sophisticated version of traditional phishing because of its use of social engineering. Spear phishing targets particular people or organizations through emails tailored specifically to deceive the victim.
Before a trap is set, spear phishers will collect data on the internet, social media and the dark web about a person or a company to create a highly specific and believable scam, providing a false sense of security before attempting to steal a victim’s personal information.
Typically, a target will receive a highly personalized email from a hacker posing as a reputable business, a government agency or even a boss or coworker. It’s difficult to spot a spear phishing email because the details inside the message usually contain accurate and convincing information.

Spear Phishing Consequences
Falling for a spear phishing attack can not only give a hacker your company’s financial information, but it can also span across your entire network.
CEO fraud, credit card fraud and domain fraud continue to be the most common consequences of an attack. Depending on the level of infiltration and the size of your business, this could result in major financial losses. What’s worse, if a successful spear phishing goes unnoticed, it increases the risk of large and continued losses.
What Helps Protect from Spear Phishing?
Now that you understand the risks, it’s important to know what helps protect from spear phishing. Tactics are constantly evolving, so spear phishing can be extremely tricky to spot, even for cybersecurity-savvy employees.
Here are five critical steps your organization can take now to protect your company and your employees against an attack:

1. Keep Your Employees Informed of Spear Phishing Signs
Employee training is one of the most important tactics when it comes to what helps protect from spear phishing. There are telltale spear phishing signs you can train your employees to look for so they don’t fall victim to a fraudulent email.
At first glance, everything in the email may look trustworthy, but the sender’s email address typically does not match up with their name or the company they are emailing from.
For example, an email from Amazon should come from <@amazon.com> whereas a spear phishing email might claim to be from Amazon, yet their email address is <amazon011@gmail.com> which is highly suspicious and should not be opened.
The sender might also try to instill a sense of urgency in their message, so the employee feels compelled to take action immediately. They may say something like, “I’m stuck in a meeting and I need you to call this number for me right away and provide them with what they ask for!” or “Please approve and pay this invoice. It’s urgent.”
Making cybersecurity a company focus and conducting regular cyber-awareness trainings is one of the most successful techniques for protecting your company from a spear phishing attack.
2. Implement a Security Policy with Password Considerations
All companies should have a strong cybersecurity policy in place, and an essential part of any cybersecurity policy is password management.
Because spear phishers are using social engineering to collect as much information on their victim as possible, it’ important to remind employees to never give anyone (even those they may trust) their password.
When it comes passwords, people tend to go with the simplest password possible. Ensure that your system has numerous password complexity requirements in place, and when it comes to password updating, do not allow employees reuse their old password by simply changing the numbers at the end.
To protect from spear phishing it’s also important that your cybersecurity policy sets stringent requirements for password expiration and complexity. Automated password expiration shortens the length of time that a cyber criminal can access an account. Even if an account is hacked, this will prevent a thief from returning to the account in the future to steal even more data.
In addition to setting password requirements, a cybersecurity policy should also include an outline on email security measures, a business continuity plan, a remote access policy, a data breach response policy and a disciplinary action plan.
3. Utilize Multi-Factor Authentication and a VPN
Multi-factor authentication requires users to provide two or more methods of verification for access to a system.
Multi-factor authentication combines a standard login and password paired with additional verification factors, such as biometrics, app-based authentication and text messaging. This is one of the simplest and most cost-effective methods for improving your cybersecurity.
By simply adding these extra checkpoints, you can keep your business protected from spear phishing and ransomware—and stop hackers in their tracks.
A Virtual Private Network (VPN) is also a great way to protect your business from cyber attacks. This will allow you to encrypt your network traffic to enhance protection and ensure privacy.
The right VPN adds an extra layer of protection for your company’s network, even if your employees are working remotely. This tool is highly recommended and especially crucial when sensitive company information is being shared.
4. Encrypt Files and Keep Backups
Encrypting your files safeguards them from being hacked because only those with a decryption key will be able to access them.
Although programs that claim they can decrypt your encrypted file do exist, they often aren’t effective. Nevertheless, installing a skilled encryption system will allow you to know your data is protected from spear phishing.
While backing up data is a standard best practice to keep important information from getting lost, it’s also a means of protecting your business. Keeping backups is an effective way of safekeeping your files in the event of an attack, and it can allow you to figure out how the cyber criminal got in so you can prevent future attacks.
You’ll also be able to change your passwords, restore your files and keep your business running as usual. To ensure backups are the most effective, be sure to keep copies offline and test them regularly. Some ransomware attacks search specifically for unencrypted backups, as well as production data to increase the effectiveness of the attack.
5. Make Sure That Your Security Software is Up to Date
When it comes to what helps protect from spear phishing, security software is a lifesaver. Unprotected systems are at a big risk for viruses and malware, which is why it’s ideal to have both antivirus and antimalware software installed.
While your software may suggest updates, it can be easy to overlook or put off until another time. As a best practice, configure your systems to install updates automatically so you don’t leave them vulnerable to an attack.
This type of patching will help ensure that operating systems, applications and firmware are all updated in a timely manner, so your business stays protected from spear phishing.
Learn More about What Helps Protect from Spear Phishing
If you’d like to learn more about what helps protect from spear phishing, or if you need guidance on what to do next if your business falls victim to a spear phishing attack, speak with a Warren Averett Technology Group expert today.

